In the labyrinth of cyber threats that besiege the digital realm, one particularly stealthy adversary lurks beneath the surface, wielding the power to redirect innocent internet users to treacherous terrains. DNS poisoning, a deceptive manipulation within the Domain Name System (DNS), poses a formidable risk, masquerading as legitimate pathways while leading unsuspecting users astray. This comprehensive guide aims to answer the question of what is DNS poisoning and how to prevent it.
We’ll explore its covert tactics, unraveling its implications, and equipping individuals and enterprises with effective shields against its pernicious influence. Join us on this journey through the intricate web of DNS security as we delve into the depths of this cyber threat and unveil robust strategies to fortify our digital bastions against its surreptitious incursions.
Understanding the Domain Name System (DNS)
Before answering the question of what is DNS poisoning and how to prevent it, let’s see what DNS is in essence. The Domain Name System (DNS) serves as the internet’s essential directory, translating easily memorable domain names into numeric IP addresses that computers understand. Operating behind the scenes, DNS ensures that when a user types in a website address, their device connects to the correct server, enabling access to desired online resources.
This hierarchical system comprises DNS servers and recursive resolvers, working in tandem to swiftly resolve domain queries and facilitate seamless Internet browsing experiences. By translating human-readable domain names into machine-readable IP addresses, DNS plays a crucial role in the fundamental functioning of the internet, underpinning every online interaction we undertake.
Understanding How DNS Poisoning Works
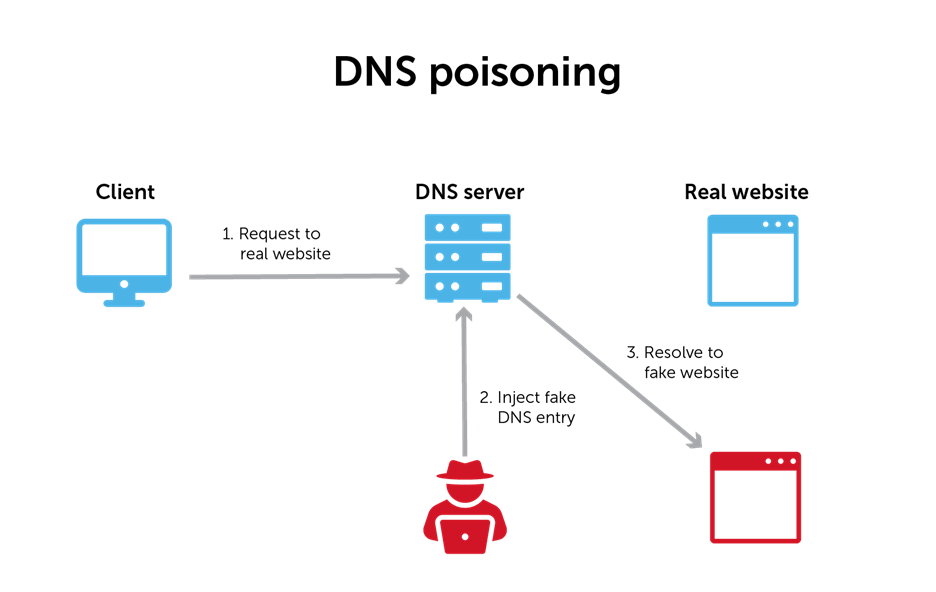
DNS poisoning operates as a surreptitious manipulation within the Domain Name System (DNS), exploiting vulnerabilities in the process of translating domain names to IP addresses. This insidious attack involves the alteration of DNS data within the system, leading unsuspecting users astray by redirecting their queries to malicious destinations.
When a user initiates a request by entering a domain name into a web browser, the typical DNS lookup process begins. However, in a DNS poisoning attack, malicious actors intercept this process at various points. By injecting false information into the DNS cache or altering DNS records on compromised servers, these attackers deceive the DNS resolver into providing incorrect IP address information associated with a particular domain.
Implications of DNS Poisoning
The ramifications of DNS poisoning are far-reaching. Attackers leverage this exploit to redirect users to deceptive websites resembling legitimate ones, often employed for phishing attacks aimed at harvesting sensitive information like passwords or financial data. Moreover, these attacks can propagate malware by diverting users to sites hosting malicious content, compromising the security and integrity of their devices.
How DNS cache poisoning works
DNS cache poisoning operates as a sophisticated cyber attack aimed at infiltrating the caching mechanism of DNS servers, thereby injecting falsified data into the cache to redirect users to malicious destinations. This nefarious tactic takes advantage of vulnerabilities within the DNS caching infrastructure, allowing attackers to manipulate the stored DNS information and potentially deceive unsuspecting users seeking legitimate websites.
Mechanism of DNS Cache Poisoning
DNS cache poisoning exploits DNS server caching. Attackers flood the DNS resolver with fake responses, aiming to replace genuine data in the cache. When these false entries infiltrate the cache, subsequent users querying the same domain may unknowingly be directed to deceptive IP addresses controlled by attackers. This manipulation redirects users to fraudulent sites, enabling cyber threats like phishing, malware distribution, and data theft.
Persistence of DNS Cache Poisoning
The challenge with DNS cache poisoning lies in the persistence of the falsified data within the cache. Even after identifying and mitigating the initial attack, the compromised DNS resolver continues to serve the malicious IP addresses stored in its cache until the records expire or are manually purged. As a result, unsuspecting users may continue to be redirected to malicious sites despite the attack being detected and mitigated on the server side.
Mitigating DNS Cache Poisoning
To combat DNS cache poisoning, network administrators implement several preventive measures. These include reducing the time-to-live (TTL) values of cached records, and ensuring frequent cache refreshing to minimize the lifespan of potentially poisoned entries. Furthermore, deploying robust security protocols such as DNS Security Extensions (DNSSEC) can fortify DNS infrastructure by cryptographically verifying the authenticity of DNS responses, thwarting attempts at cache manipulation.
Real-World Instances of DNS Poisoning
Over the years, several high-profile instances have spotlighted the pervasive threat posed by DNS poisoning, showcasing its potential to disrupt internet connectivity and compromise user security on a global scale. To understand what is DNS poisoning and how to prevent it, let’s explore some real life examples:
The Great Firewall of China:
China’s “Great Firewall” is emblematic of DNS manipulation at a national level. Operating as a massive censorship tool, it employs DNS poisoning to redirect users attempting to access restricted or unsanctioned websites, effectively controlling the information flow within the country. Instances abound where Chinese DNS servers reroute requests to unauthorized sites like Twitter or Facebook, effectively censoring content and manipulating users’ access to information.
Global Impact of Hijacked Servers:
Incidents involving compromised DNS servers illustrate the global impact of DNS poisoning. A notable case emerged when a Swedish ISP encountered a networking error, inadvertently serving root DNS information from Chinese servers. This mishap resulted in users in regions like Chile and the US being redirected away from intended websites, leading to disruptions and raising concerns about the integrity of the internet’s DNS infrastructure.
Cyber Attacks and DNS Manipulation:
Moreover, cyber attacks orchestrated by skilled hackers often leverage DNS poisoning techniques to propagate their nefarious agendas. Instances where Bangladeshi hackers hijacked multiple domains, including those related to prominent entities like Microsoft, Google, and YouTube, underscore the risks posed by server manipulation. Even organizations like WikiLeaks fell victim to potential server hijacks, redirecting unsuspecting visitors to pages controlled by attackers, emphasizing the pervasive threat of DNS-based cyber attacks.
How To Prevent DNS Poisoning
Preventing DNS poisoning requires a multifaceted approach encompassing both server-side and client-side strategies to fortify DNS infrastructure and enhance overall cybersecurity. Here are key preventive measures:
Implement DNS Security Extensions (DNSSEC)
Implementing DNS Security Extensions (DNSSEC) is a crucial step in safeguarding DNS infrastructure against potential poisoning attacks. DNSSEC adds cryptographic authentication to DNS data, ensuring its integrity and authenticity. To implement DNSSEC effectively:
- Enable DNSSEC by signing authoritative DNS zones with cryptographic keys and digital signatures.
- Configure registrars and DNS resolvers to support and validate DNSSEC signatures.
- Conduct regular audits, key management, and stay updated on DNSSEC best practices.
- Test in a controlled environment before gradual deployment, collaborating with providers for compliance.
Reduce DNS Cache Lifespan
Reducing the DNS cache lifespan is a pivotal strategy in mitigating the impact of DNS cache poisoning. By decreasing the Time-to-Live (TTL) values for cached records within DNS servers, organizations can limit the duration of stored entries. This shorter cache lifespan minimizes the window of opportunity for potential attackers to exploit poisoned data within the cache, thereby reducing the risk posed by DNS cache poisoning attacks.
To implement this preventive measure effectively:
- Adjust TTL Values: Configure DNS caching servers to lower the TTL values for cached records.
- Balancing Security and Performance: Strike a balance between security and performance when adjusting TTL values. Experiment and fine-tune TTL settings to optimize security measures without significantly compromising system performance.
- Regular Monitoring and Adjustment: Continuously monitor and evaluate the effectiveness of reduced TTL settings. Regularly review and adjust TTL values as needed based on evolving security needs and system performance requirements.
Regular Security Audits and Updates
Regular security audits and updates play a critical role in fortifying DNS infrastructure against potential vulnerabilities and evolving threats. These proactive measures involve continuous assessment and maintenance of DNS servers to identify and address security gaps. Here’s how to implement them effectively:
- Scheduled Audits: Conduct routine audits of DNS servers and resolver software. Check for known vulnerabilities, configuration errors, and outdated software that could be exploited by attackers. Use automated scanning tools or engage cybersecurity experts for comprehensive audits.
- Patch Management: Ensure timely installation of security patches, updates, and firmware upgrades provided by DNS server vendors or open-source communities. Regularly apply security patches to address newly discovered vulnerabilities and strengthen system defenses.
- Configuration Review: Regularly review DNS server configurations for any misconfigurations or weak settings that could pose security risks. Validate access controls, authentication mechanisms, and logging configurations to enhance overall security posture.
Implement Firewall and Intrusion Prevention Systems
Implementing robust firewall and intrusion prevention systems (IPS) forms a critical defense layer against DNS-based attacks, including DNS poisoning. These systems act as frontline security measures, monitoring and controlling incoming and outgoing network traffic to detect and block malicious activities targeting DNS infrastructure. Here’s how to deploy these systems effectively:
- Firewall Deployment:
- Network Segmentation: Segment the network to isolate critical DNS servers and establish firewall rules that permit authorized traffic while blocking unauthorized access.
- Stateful Packet Inspection (SPI): Configure firewalls with SPI to inspect incoming and outgoing packets, identifying and blocking potentially harmful data packets.
- Intrusion Prevention Systems (IPS):
- Signature-Based Detection: Deploy IPS solutions equipped with signature-based detection to identify known patterns of malicious DNS traffic, preventing attacks based on recognized signatures.
- Behavioral Analysis: Utilize IPS systems employing behavioral analysis to detect anomalies in DNS traffic behavior, swiftly identifying and blocking suspicious activities.
- Regular Updates and Configurations:
- Update Signatures and Rules: Ensure IPS and firewall systems are regularly updated with the latest threat signatures, patches, and rule sets to defend against new attack vectors and vulnerabilities.
- Fine-tuning and Optimization: Regularly review and fine-tune firewall and IPS configurations to adapt to changing network environments and emerging threats, optimizing security effectiveness.
Educate Users and Employees
Promote awareness among users and employees regarding phishing threats, suspicious links, and the importance of verifying website authenticity. Encourage practices like avoiding clicking on unrecognized links, utilizing secure browsing habits, and validating SSL certificates to mitigate the risk of falling victim to DNS-based attacks.
Regular Monitoring and Response Protocols
Implement robust monitoring tools and response protocols to detect and swiftly respond to suspicious DNS activity. Establish procedures for immediate investigation and remediation in the event of suspected DNS poisoning incidents, minimizing potential damage and restoring DNS integrity promptly.
Wrapping Up
In conclusion, DNS poisoning remains a prevalent and insidious threat, capable of manipulating the Domain Name System to redirect users to fraudulent websites, compromise data integrity, and facilitate various cyber threats. This sophisticated form of attack exploits vulnerabilities within DNS infrastructure, highlighting the critical need for robust preventive measures to fortify against potential breaches.
Implementing advanced security protocols like DNSSEC, reducing DNS cache lifespans, and ensuring regular software updates serve as crucial steps in fortifying DNS servers against poisoning attempts. Additionally, fostering user awareness, employing intrusion prevention systems, and maintaining vigilant monitoring practices contribute significantly to enhancing the overall cybersecurity posture against DNS-based attacks.